Home · Tags · Software

Digital Design - An Embedded Systems Approach Using VHDL
2017-12-27
The book assumes a basic understanding of the general principals, concepts, and components of electrical engineering. These basic concepts are expanded upon with more detailed descriptions of digital logic/boolean algebra and slightly more abstracted complex components like flip-flops. These abstractions are introduced and modeled, usually in a well described UML style presentation, and then converted into VHDL. As it progresses, the book combines all of the aforementioned into more complex designs that include finite state machines, soft cores, memories, accelerators, etc. Before a final review of the design process, a case study is presented for the design of a pipelined implementation of a sobel filter video accelerator.

FPGA 101 - Everything You Need to Know to Get Started
2017-12-02
This book seemed great for a beginner with its inclusion of a nice list of acronyms, and with all the new terminology was well defined. It starts with the (sometimes too) basics, giving simple examples snippets of VHDL date types and code as well as general programming tips such as commenting and code organization. The connection between hardware and software is well described and elucidate with various diagrams of simple examples of logic gates and their equivalent VHDL. There is a fuller example, complete with VHDL and test bench code, that is used repeatedly for the last part of the book that is complex enough to be interesting and well described enough to follow. The last three-quarters of the book focuses more on the design process phases including- design, simulation, synthesis, implementation, and programming.

Firefox Session Saver
2017-09-10
A simple script to backup and restore your Firefox session without the need for flaky addons.

Custom Traffic Parser and Plotter
2017-06-27
This simple pair of programs extracts apache's logs into JSON and creates simple bar graphs via matplotlib.

Image Notes HTML Parser
2017-03-25
A simple program to generate the HTML (jinja) for all the image notes associated with a book.
Mastering Kali Linux for Advanced Penetration Testing
2017-01-06
The first part deals with identifying a target and then performing active and passive reconnaissance to lookup DNS records, conduct port scans, and utilize various open source intelligence techniques, among many other options. Next, vulnerability databases and tools, like Metasploit and Veil Evasion, that give easy access to potential access points to a system are covered alongside a lighter look at things like shellcode. Less technical attack vectors are explored when looking at social engineering attacks, like spoofing a website, that can be quickly created with tools like SET, the Social Engineers Toolkit. The ubiquitousness of wireless access demands its inclusion but is only touched upon as a general introduction to a potentially detailed topic. Lastly, web application vulnerabilities are tested with frameworks like Beef with some minor asides into some of the specific vulnerabilities - like SQL injection.

World Geo-Graph-y
2016-10-09
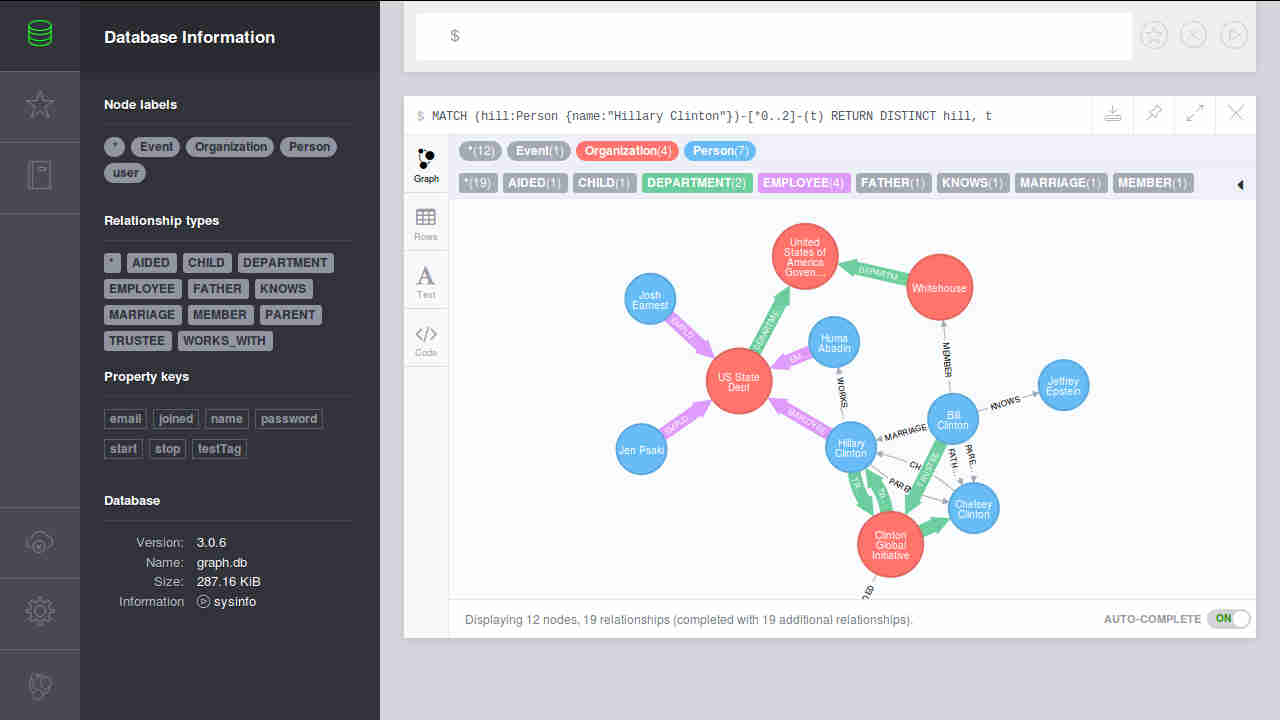
This is an article about how to rip the country land border data from wiki, reformat it, and dump it into a neo4j graph.

O'reilly Graph Databases
2016-10-05
Graphs often map more naturally to the entities (nodes) and their relationships than 'traditional' RDBMS do. Business and technical sides can now communicate because the whiteboard model is the model. The questions you want to ask of your data will drive how to model your graph. Graphs, as opposed to other NOSQL databases, retain ACID transactions, fast lookups, and scalability. While there is no one-size-fits all database solution, graphs are a formidable option in any realm and really shine with densely connected datasets.

Khan Academy Video Sorter
2015-09-23
From one messy folder containing almost 5000 hashed video names to a neatly organized hierarchical structure in 25 lines of python.

Building Web Applications with Python and Neo4j
2015-01-01
The first half focuses on setting up the software and interacting with your first graph database using cypher. The second half is overloaded with basic Flask and Django based tutorials alongside deployment issues like caching, fault tolerance, clustering, and other advanced features. It provides a nice overview, but a whole book could be written about each of the last three chapters.
Craigslist Scnner
2014-10-11
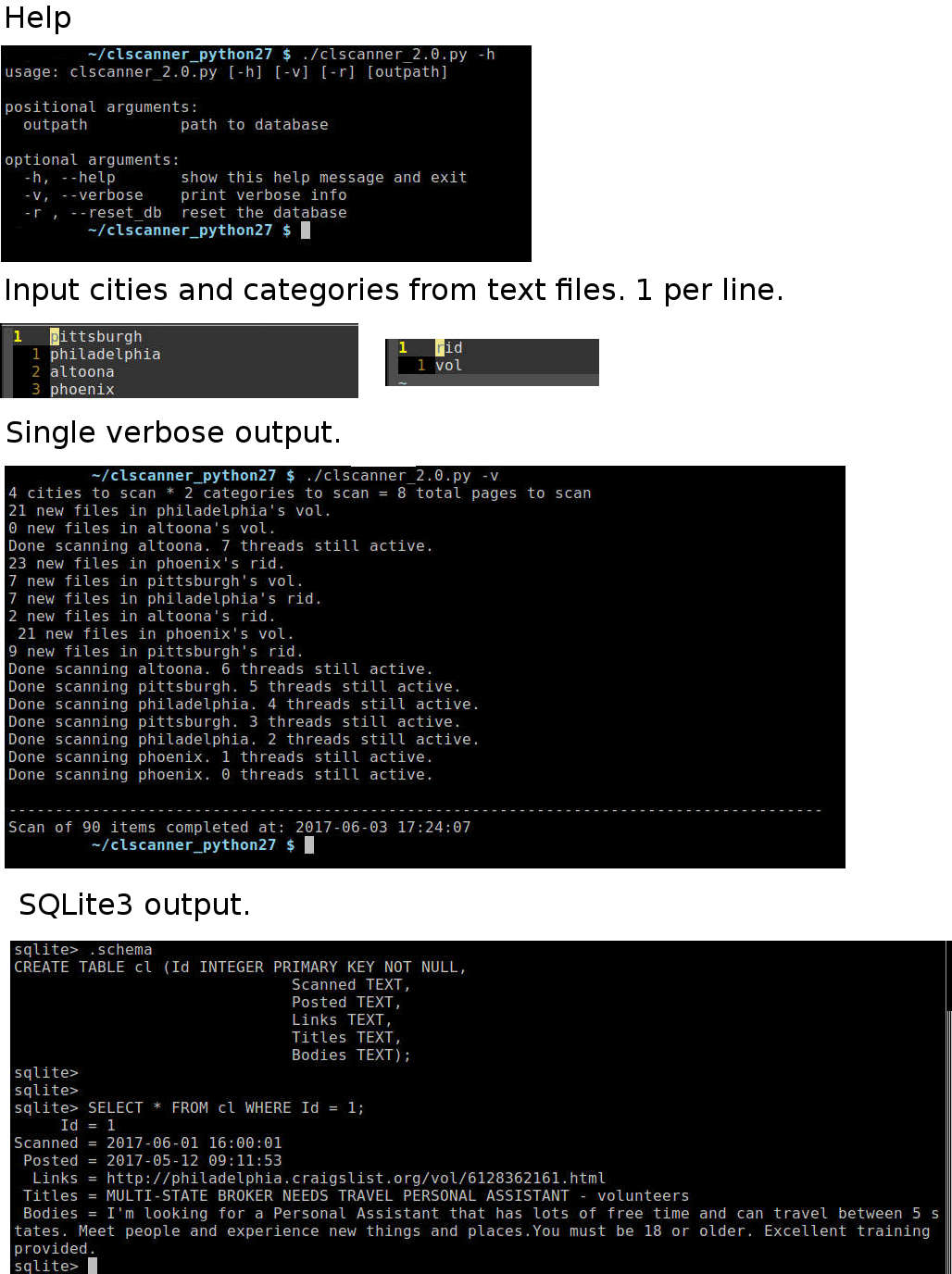
One of the first python programs I wrote, in 2014, to actually do something for me. It threadedly scans multiple craigslist cities and categories and writes everything it sees to an SQLite database. It was used to alert when new items are posted that match a given criteria and to search for non-location specific goods ie: a sailboat.
Ai
Algorithms
Animals
Apache
Army
Artificial-Intelligence
Bash
Bitcoin
Boycott
Business
Cia
Communication
Computer
Conspiracy-Theory
Creativity
Css
Culture
Cybernetics
Database
Demographics
Desk
Diabetes
Diet
Docker
Drugs
Eclipse
Economics
Education
Electronics
Encryption
Ergonomic
Evolution
Family
Fiction
Firefox
Flask
Fpga
Furniture
Games
Garden
Git
Godot
Graph
Gui
Habits
Hacking
Hardware
Health
Hiking
History
Html
Immigration
Java
Json
Keto
Lgbt
Linux
Machine Learning
Marketing
Math
Matplotlib
Melatonin
Military
Motivation
Music
Neo4j
Notes
Numpy
Occult
Oligarchy
Pedophilia
Permaculture
Philosophy
Physics
Politics
Posture
Programming
Propaganda
Protest
Psychology
Psyop
Python
Python"
Rabbits
Regex
Religion
Research
Sci-Fi
Scipy
Sleep
Social
Software
Sqlite
Suicide
Technology
Travel
Vhdl
Vim
Waterfall
Woodworking
Writing