Home · Book Reports · 2017 · Mastering Kali Linux for Advanced Penetration Testing
- Author :: Robert Beggs
- Publication Year :: 2014
- Read Date :: 2017-01-06
- Source :: Mastering_Kali_Linux_For_Advanced_Penetration_Testing.pdf
designates my notes. / designates important.
Thoughts
A good general introduction to what you can do with Kali, for the most part out of the box, but I’d have to say “Mastering” and “Advanced” is a bit of a stretch. Given the breadth of topics covered, each of which can be explored in books of their own, the information is, although sometimes dated, top-notch.
For example, something like nmap is covered only in the most basic how to use sense. Although intrusion detection systems are mentioned, and the noisiness of scans also mentioned, there is nothing that would be considered advanced. There is a small library of books written on nmap alone while it is only one of dozens of programs highlighted in this one.
Table of Contents
- Chapter 1: Starting with Kali Linux
- Chapter 2: Identifying the Target – Passive Reconnaissance
- Chapter 3: Active Reconnaissance and Vulnerability Scanning
- Chapter 4: Exploit
- Chapter 5: Post Exploit – Action on the Objective
- Chapter 6: Post Exploit – Persistence
- Chapter 7: Physical Attacks and Social Engineering
- Chapter 8: wireless
- Chapter 9: Reconnaissance and Exploitation of Web-based Applications
- Chapter 10: Exploiting Remote Access Communications
- Chapter 11: Client-side Exploitation
- Appendix
· Chapter 1: Starting with Kali Linux
page 36:
- instanbul: This is a desktop screen recorder that allows you to make a movie of desktop activities.
· Chapter 2: Identifying the Target – Passive Reconnaissance
page 45:
- The US Army manual ATP 2-22.9 (http://www.fas.org/ irp/doddir/army/atp2-22-9.pdf) and the NATO OSINT manual (http://information-retrieval.info/docs/ NATO-OSINT.html) are both available online, and provide excellent technical reviews of how to gather and assess OSINT.
page 46:
page 47:
-
Sites that provide lookups of DNS, route, and server information, especially, DNSstuff (www.dnsstuff.com), ServerSniff (www.serversniff.net), Netcraft (www.netcraft.com), and myIPneighbors.com
-
Shodan (www.shodanHQ.com), sometimes referred to as the “hacker’s Google”; Shodan lists Internet-accessible devices and allows the tester to search for devices with known vulnerabilities
-
Password dumpsites (pastebin, search using site:pastebin.com “targetURL”)
page 51:

page 54:
- Using a web-based traceroute (www.traceroute.org), it is possible to trace various geographic origin sites to the target network. These types of scans will frequently identify more than one different network connecting to the target, which is information that could be missed by conducting only a single traceroute from a location close to the target. Web-based traceroute may also identify multihomed hosts which connect two or more networks together. These hosts are an important target for attackers, because they drastically increase the attack surface leading to the target.
page 55:
- In Kali, traceroute is a command-line program that uses ICMP packets to map the route; in Windows, the program is tracert.
page 56:

· Chapter 3: Active Reconnaissance and Vulnerability Scanning
page 67:
-
it is possible for the DHCP to interact with the target system, which could be logged and send alarms to the target’s administrators.
-
Some commercial and open source tools (for example, the Metasploit Framework) tag their packets with an identifying sequence. Although this can be useful in post-test analysis of a system’s event logs (where events initiated by a particular testing tool can be directly compared to a system’s event logs to determine how the network detected and responded to the attack), it can also trigger certain intrusion detection systems. Test your tools against a lab system to determine the packets that are tagged, and either change the tag, or use the tool with caution.
-
search the packet capture (pcap) files for the any keywords that can be attributed to the testing tool (name of the tool, vendor, license number, and so on).
page 68:
-
Identify the goal of the scan before testing and send the minimum number of packets needed to determine the objective. For example, if you wish to confirm the presence of a web host, you first need to determine if port 80 , the default port for web-based services, is open.
-
Avoid scans that may connect with the target system and leak data. Do not ping the target or use synchronize (SYN) and nonconventional packet scans, such as acknowledge (ACK), finished (FIN), and reset (RST) packets.
-
Randomize or spoof packet settings, such as the source IP and port address, and the MAC address.
-
Adjust the timing to slow the arrival of packets at the target site.
-
Change the packet size by fragmenting packets or appending random data to confuse packet inspection devices.
page 69:
- tor stuff and dns leaking
page 74:
-
SHODAN - Web-based search engine that identifies devices connected to the Internet, including those with default passwords, known misconfigurations, and vulnerabilities
-
change ttl to confuse OS detection
page 82:
- A must-have script is the SpiderLabs script to screenshot web services. It requires the wkhtmltoimage tool to be downloaded (http:// wkhtmltopdf.googlecode.com) and placed in the /usr/local/ bin folder. The screenshot script itself should then be downloaded (https://github.com/SpiderLabs/Nmap-Tools/blob/ master/NSE/http-screenshot.nse) and placed in /usr/local/ share/nmap/scripts. When invoked, this script produces a visual record of all the identified web services, making it easier to select a target for testing later.
page 85:
- recon-ng to do the following:
- Harvest contacts using whois, jigsaw, linkedin, and twitter (use the mangle module to extract and present e-mail data)
- Identify hosts
- Identify geographical locations of hosts and individuals using hostop, ipinfodb, maxmind, uniapple, and wigle
- Identify host information using netcraft and related modules
- Identify account and password information that has previously been compromised and leaked onto the Internet (the pwnedlist modules, wascompanyhacked, xssed, and punkspider)
page 88:
- Network Scanning Watch List at www.digininja.org, for devices known to fail as a result of vulnerability testing
· Chapter 4: Exploit
- Model your attack
page 94:
-
online sites that collect, analyze, and share information about vulnerabilities are as follows:
-
The National Vulnerability Database that consolidates all public vulnerability data released by the US Government available at http://web.nvd.nist.gov/view/vuln/search
-
Secunia available at http://secunia.com/community/
-
Open Source Vulnerability Database Project (OSVDP) available at http://www.osvdb.org/search/advsearch
-
Packetstorm security available at http://packetstormsecurity.com/
-
SecurityFocus available at http://www.securityfocus.com/ vulnerabilities
-
Inj3ct0r available at http://1337day.com/
-
The Exploit Database maintained by Offensive Security available at http://www.db-exploit.com
-
The exploit database is also copied locally to Kali and it can be found in the /usr/ share/exploitdb directory. Before using it, make sure that it has been updated using the following command:
-
cd /usr/share/exploitdb
-
tar -xvjf archive.tar.bz2
-
rm archive.tar.bz2
-
To search the local copy of exploitdb, open a terminal window and enter searchsploit and the desired search term(s) in the command prompt. This will invoke a script that searches a database file (.csv) that contains a list of all exploits. The search will return a description of known vulnerabilities as well as the path to a relevant exploit. The exploit can be extracted, compiled, and run against specific vulnerabilities.
page 95:
- The search script scans for each line in the CSV file from left to right, so the order of the search terms is important—a search for oracle 10g will return several exploits, but 10g oracle will not return any. Also, the script is weirdly case sensitive; although you are instructed to use lower case characters in the search term, a search for Bulletproof FTP returns no hits, but bulletproof FTP returns seven hits, and bulletproof ftp returns no hits. More effective searches of the CSV file can be conducted using the grep command or a search tool such as KWrite (apt-get install kwrite).
page 106:
- Hail Mary Attack of Armitage is good for testing an IDS.
page 111:
- (www.Veil-Evasion.com), is now providing effective protection against the detection of standalone exploits. Veil-Evasion aggregates various shellcode injection techniques into a framework that simplifies management.
· Chapter 5: Post Exploit – Action on the Objective
page 123:
- quick recon in new system commands
page 126:
- powershell is worth learning
page 127:
- During a recent penetration test, we were prohibited from installing any executable software on the client’s systems. We used a PowerShell keylogger on a compromised system to grab administrator-level credentials and then compromised most of the systems on the network. The most effective exploit and post-exploit scripts, including the keylogger, are part of Nikhil Mittal’s Nishang package (https://code.google.com/p/nishang/downloads/detail?name=nishang_0.3.0.zip).
page 129:
-
if the compromised system is Unix, then the attacker will also target the following:
-
The system and configuration files (usually in the /etc directory, but depending on the implementation, they may be in /usr/local/etc or other locations)
-
The password files (/etc/password and /etc/shadow)
-
The configuration files and public/private keys in the .ssh directory
-
The public and private key rings that may be contained in the .gnupg directory
-
The e-mail and data files
-
In a Windows system, the attacker will target the following:
-
The system memory, which can be used to extract passwords, encryption keys, and so on
-
The system registry files
-
The Security Accounts Manager (SAM) database that contains hashed versions of the password, or alternative versions of the SAM database which may be found in %SYSTEMROOT%\repair\SAM and %SYSTEMROOT%\System32\ config\RegBack\SAM
-
Any other password or seed files used for encryption
-
The e-mail and data files
-
Don’t forget to review folders that contain temporary items, such as attachments. For example, UserProfile\AppData\Local
Microsoft\Windows\Temporary Internet Files\ may contain files, images, and cookies that may be of interest.
page 130:
-
The system memory can be downloaded as a single image file from several sources as follows:
-
By uploading a tool to the compromised system and then directly copying the memory (the tools include Belkasoft RAM capturer, MandiantMemoryze, and MonsolsDumpIt).
-
By copying Windows hibernation file, hiberfil.sys and then using Volatility to decrypt and analyze the file. Volatility, found on Kali in the Forensics menu, is a framework that was written to analyze memory dumps from the system RAM and other files containing system memory. It relies on plugins written in Python to analyze the memory and extract data, such as encryption keys, passwords, registry information, processes, and connectivity information.
-
By copying a virtual machine and converting the VMEM file to a memory file.
-
If you upload a program designed to capture memory onto a compromised system, it is possible that this particular application will be identified as malicious software by an antivirus software. Most antivirus software applications recognize the hash signature and behavior of memory acquisition software, and act to protect the sensitive contents of the physical memory by raising an alarm if it is at risk of disclosure. The acquisition software will be quarantined, and the target will receive a warning alerting them of the attack.
-
To avoid this, use Metasploit Framework to run the executable completely in the target’s memory using the following command:
-
meterpreter> execute -H -m -d calc.exe -f <memory executable + parameters>
-
The previous command executes calc.exe as a dummy executable but uploads the memory acquisition executable to run in its process space instead.
-
The executable doesn’t show up in process lists, such as Task Manager, and detection using data forensic techniques is much harder because it’s not written to disk. Furthermore, it will avoid the system’s antivirus software, which generally does not scan the memory space in search of malware.
page 131:
-
Using the sample image for a system infected with Zeus malware (https://code. google.com/p/volatility/wiki/SampleMemoryImages), we’ll use Volatility Framework to extract the encrypted LanMan password hashes.
-
using volitility on windows
page 138:
- The stdapi library allows a remote attacker to manipulate a webcam by collecting audio and video from the compromised system and relaying that data back to the attacker.
page 139:
-
dsniff is designed to extract passwords from live transmissions or a pcap file saved from a Wireshark or tshark session
-
Dump the SAM and SYSKEY files using meterpreter or applications such as hobocopy, fgdump, and pwdump (these can be uploaded on the target using meterpreter).
-
Inject malicious code directly into a service running at the SYSTEM level using a tool such as process injector (www.tarasco.org/security/Process_Injector/).
-
When some applications load, they read dynamic link library (DLL) files in a particular order. It is possible to create a fake DLL with the same name as a legitimate DLL, place it in a specific directory location, and have the application load and execute it, resulting in elevated privileges for the attacker. Several applications are known to be vulnerable to such DLL hijacking (www.exploit-db.com/dll-hijacking-vulnerable-applications/).
page 140:
-
Execute the getsystem script, which will automatically escalate administrator privileges to the SYSTEM level, from the meterpreter prompt.
-
Windows 7 and 2008 don’t allow remote access to administrative shares, such as ADMIN$, C$, and so on, from untrusted systems. These shares may be required for meterpreter scripts, such as incognito, or to support attacks over SMB. To address this issue, add HKEY_LOCAL_ MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ Policies\System to the registry, and add a new DWORD (32-bit) key named LocalAccountTokenFilterPolicy and set the value to 1.
· Chapter 6: Post Exploit – Persistence
· Chapter 7: Physical Attacks and Social Engineering
page 187:
- Note that the address in the URL bar is not the valid address for Google; most users will recognize that something is wrong if they can see the address. A successful exploit requires the attacker to prepare the victim with a suitable pretext, or story, to make the victim accept the unusual URL. For example, send an e-mail to a targeted group of nontechnical managers to announce that a “local Google mail site is now being hosted by IT to reduce delays in the mail system.”
page 188:
-
The Credential harvesting attack is an excellent tool for assessing the security of a corporate network. To be effective, the organization must first train all employees on how to recognize and respond to a phishing attack. Approximately two weeks later, send a corporate-wide e-mail that contains some obvious mistakes (incorrect name of the corporate CEO or an address block that contains the wrong address) and a link to a program that harvests credentials. Calculate the percentage of recipients who responded with their credentials, and then tailor the training program to reduce this percentage.
-
Are people so gullible that “obvious mistakes” must, intentionally, be included?
page 194:
- DNS redirection with ettercap
· Chapter 8: wireless
page 205:
root@kali:~# iwconfig wlan0 txpower 30
root@kali:~# airmon-ng start wlan0
root@kali:~# airmon-ng check kill
page 206:
- To view the local wireless environment, use the following command:
root@kali:~# airodump-ng mon0
root@kali:~# aireplay-ng -9 mon0 //-9 indicates an injection test
root@kali:~# kismet
page 208:
- When Kismet is launched, you will be faced with a series of questions that will allow you to configure it during the start up process. Respond with Yes to Can you see colors, accept Kismet is running as root, and select Yes to Start Kismet Server. In the Kismet start up options, uncheck Show Console as it will obscure the screen. Allow Kismet to start.
page 209:
- Enable your wireless interface by entering the following (you may need to replace wlan0 with an available wireless interface that was identified in the previous step): root@kali:~# airmon-ng start wlan0
page 210:
-
If you reconfirm with ifconfig, you will see that there is now a monitoring or mon0 address in use. Now, use airodump to confirm the available wireless networks, as given in the following command:
root@kali:~# airodump-ng mon0 -
root@kali:~# airodump-ng -c 6 mon0Executing the command removes the output from the multiple wireless sources, and allows the attacker to focus on the target ESSID
page 211:
- deauthenticate attack
page 212:
- Chamge MAC (must be offline):
root@kali:~# ifconfig wlan0 down
root@kali:~# ifconfig wlan0 | grep HW
root@kali:~# ifconfig wlan0 hw ether 38:33:15:xx:xx:xx
root@kali:~# ifconfig wlan0 up
- tool to change MAC to random of the correct vendor
root@kali:~# macchanger wlan0 -e
- To change the existing MAC address to a completely random MAC address, use the following command:
root@kali:~# macchanger wlan0 -r
page 213:
- Some attackers use automated scripts to change their MAC addresses on a frequent basis during testing to anonymize their activities.
page 214:
- WEP attack
page 218:
-
Fern GUI for aircrack-ng
-
wifite text base aircrack-ng frontend
page 220:
- WPA attack
page 222:
- GPU-based password cracking tools (oclHashcat for AMD/ATI graphics cards and cudaHashcat for NVIDIA graphics cards).
page 223:
-
To implement this attack, first convert the WPA handshake capture file, psk-01.cap to a hashcat file using the following command:
root@kali:~# aircrack-ng psk-01.cap -J <output file> -
When the conversion is completed, run the hashcat against the new capture file (choose the version of hashcat that matches your CPU architecture and your graphics card) using the following command:
root@kali:~# cudaHashcat-plus32.bin -m 2500 <filename>.hccap <wordlist> -
Reaver WPA attack
page 224:
- Cloning Access Points
page 226:
-
Denial of service
-
websploit
· Chapter 9: Reconnaissance and Exploitation of Web-based Applications
page 232:
- The wafw00f script is an automated tool to identify and fingerprint web-based firewalls; testing has determined that it is the most accurate tool for this purpose.
page 233:
- Load balancing detector (lbd) is a bash shell script that determines if a given domain uses DNS and/or HTTP load balancing.
page 234:
- Kali supports several web crawlers, including Burp Suite, DirBuster, OWASP-ZAP, Vega, WebScarab, and WebSlayer. The most commonly used tool is DirBuster.
page 238:
- OWASP Mantra - Firefox plugin vuln scanner
page 240:
- Vulnerability scanners are quite “noisy”, and are usually detected by the victim. However, scans frequently get ignored as part of regular background probing across the Internet. In fact, some attackers have been known to launch large-scale scans against a target to camouflage the real attack or to induce the defenders to disable detection systems to reduce the influx of reports that they have to manage.
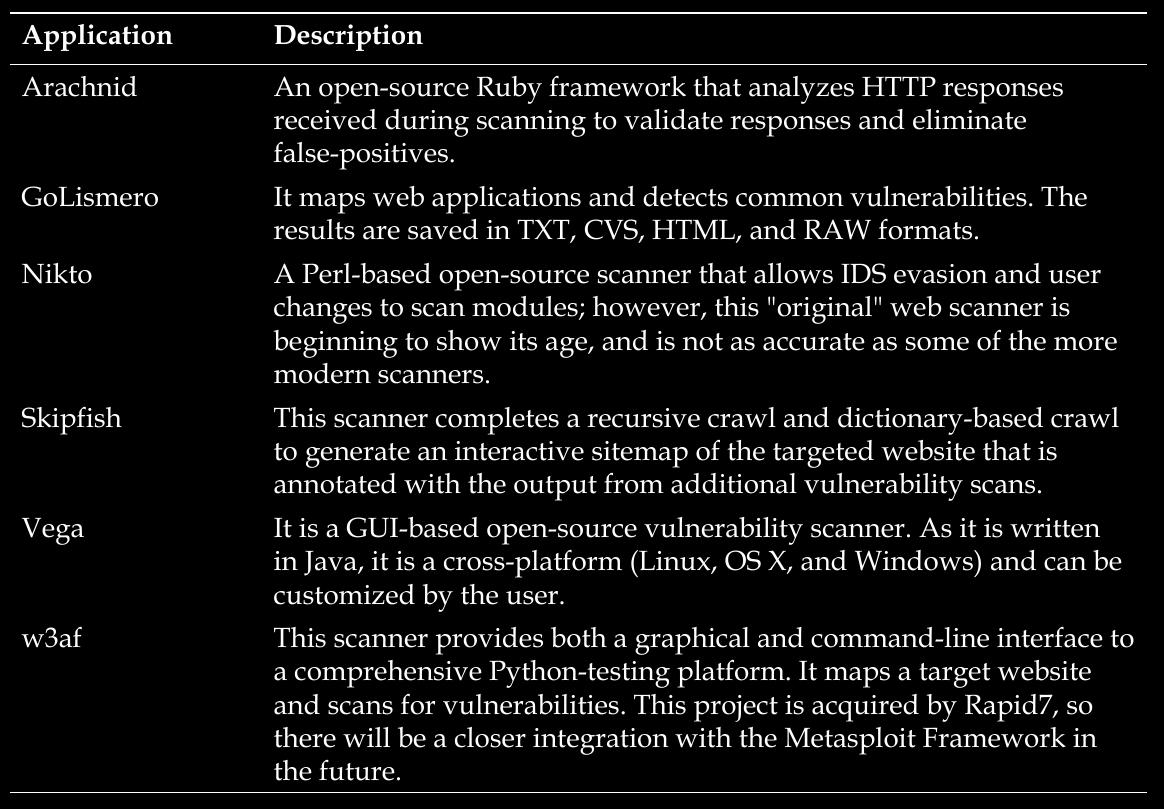
page 241:
- Most testers start testing a website by using Nikto, a simple scanner (particularly with regards to reporting) that generally provides accurate but limited results

page 242:
-
Next can use a more complete scanner, like, vega
-
Another scanner worth using is the Web Application Attack and Audit Framework (w3af), a Python-based open-source web application security scanner. It provides preconfigured vulnerability scans in support of standards such as OWASP. The breadth of the scanner’s options comes at a price—it takes significantly longer than other scanners to review a target, and it is prone to failure over long testing periods.
page 243:
- WPScan is used specifically against WordPress CMS applications.
page 244:
- Burp overview
page 250:
- Download the LOIC from GitHub (https://github.com/NewEraCracker/LOIC/downloads
page 252:
-
Kali comes with hydra, a command-line tool, and hydra-gtk, which has a GUI interface. Both tools allow a tester to brute force or iterate possible usernames and passwords against a specified service. Multiple communication protocols are supported, including FTP, FTPS, HTTP, HTTPS, ICQ, IRC, LDAP, MySQL, Oracle, POP3, pcAnywhere, SNMP, SSH, VNC, and others.
-
One of the most useful tools for assessing SQL injection vulnerabilities is sqlmap, a Python tool that automates the reconnaissance and exploitation of Firebird, Microsoft SQL, MySQL, Oracle, PostgreSQL, Sybase, and SAP MaxDB databases.
page 254:
- popular PHP web shell called Weevely. Weevely simulates a Telnet session
· Chapter 10: Exploiting Remote Access Communications
page 258:
- the most common compromise of RDP is using social engineering. The user is contacted by a remote service technician who convinces the user that they need remote access to fix something
page 259:
-
RDP port 3389
-
The nmap tool now includes specialized scripts that provide additional details about RDP, including the configuration of the encryption. If time permits, and if stealth is not an issue, these should be used during the initial scanning stage. The command line to invoke the script that enumerates supported encryption protocols is as follows:
root@kali:~# nmap – p 3389 –-script rdp-enum-encryption <IP> -
The nmap tool now includes specialized scripts that provide additional details about RDP, including the configuration of the encryption. If time permits, and if stealth is not an issue, these should be used during the initial scanning stage. The command line to invoke the script that enumerates supported encryption protocols is as follows:
root@kali:~# nmap – p 3389 –-script rdp-enum-encryption <IP>
page 260:
-
target-specific dictionaries can also be constructed to be target specific using tools such as CeWL and crunch
-
Kali provides several tools to brute-force access, including hydra, medusa, ncrack, and patator. Through testing, we have found ncrack to be the most reliable
page 261:
- The ncrack tool is a high-speed authentication cracking tool that supports
the FTP, HTTP(S), POP3, RDP, SMB, SSH, Telnet, and VNC protocols. It is
invoked from the terminal window using the following command:
root@kali:~# ncrack -vv -U user.lst -P password.list <Taget IP>:<Target Port>
page 262:
root@kali:~# hydra -s 22 -v -V -L <file path/name> -P <file path/name> -t 8 <Target IP><protocol>
- The command parameters are described in the following list:
-s designates the port to be used. Although it does not need to be entered when the default port is intended to be used, it is used to remove ambiguities and because it speeds up testing, in this case.-vand-Vselect the maximum verbosity of reports.-Lselects the login, or username file.-Pselects the password file.-tselects the number of parallel tasks or connections. The greater the number, the faster the testing will occur. However, if the number is too high, errors may be introduced and correct passwords will be missed.
page 267:
- Configuring Kali for SSLv2 scanning
page 271:
- SSL scanning tools
page 274:
- A new tool that is presently emerging from development is OWASP’s O-Saft (www.owasp.org/index.php/O-Saft), which provides a comprehensive overview of the SSL configuration, ciphers, and certificate data.
page 275:
- Using sslstrip to conduct a man-in-the-middle attack
page 278:
- Attacking an IPSec Virtual Private Network
page 283:
- VulnVPN (www.rebootuser.com) is a virtual operating system and vulnerable VPN server. It allows you to apply the tools described in this chapter to compromise the application and gain root access without damaging a production system.
· Chapter 11: Client-side Exploitation
page 286:
- VBScript
page 289:
- Powershell
page 292:
- Cross-Site Scripting Framework (XSSF)
page 299:
- BeEF
· Appendix
page 316:
- Full disk encryption and nuking the master key
page 325:
-
The database specified in the Mutillidae configuration file is incorrect, and you may receive multiple errors for operations that require database access. To fix these, log in to Metasploitable2 and edit the
/var/www/mutillidae/config.incfile; change the dbname field from metasploit to owasp10. -
Hackxor: This is a web application hacking game that forces players to progress through a story to solve challenges related to various vulnerabilities (http://hackxor.sourceforge.net/cgi-bin/index.pl).
-
Foundstone: This has released a series of vulnerable web applications, including a bank, bookstore, casino, shipping, and a travel site (www.mcafee.com/us/downloads/free-tools/index.aspx).
-
OWASP Broken Web Applications Project: This is a collection of vulnerable web applications (http://code.google.com/p/owaspbwa/).
-
WebGoat: This is an insecure J2EE web application that attempts to provide a realistic testing environment. It is maintained by OWASP (https://www.owasp.org/index.php/Category:OWASP_WebGoat_Project).
-
Web Security Dojo: This training application released by Maven Security (https://www.mavensecurity.com/web_security_dojo/), contains several target images, including Damn Vulnerable Web App, Google’s Gruyere, Hackme’s Casino, OWASP’s Insecure Web App and WebGoat, w3af’s test website, and several vulnerability-specific targets. It also contains a toolset to support exploitation.